Neophyte
Federated Authentication flow - AWS Cognito as IDP - Microsoft Entra MultiTenant app
Federated authentication flow fails to conclude with the following error message:
error_description=Bad+id_token+issuer+https://login.microsoftonline.com/{{tenant_uuid}}/v2.0&error=invalid_request
Landscape:
- Globally unique ASP.NET web application responsibe to conclude with the initial authentication (.NET 8.0 ASP.NET hosting an Angular client app + providing backend API for auth flows)
- AWS Cognito as Identity provider
- Azure Enterprise application (Multitenant) which is used for the authentication process
1. The user clicks the "Sign in with Microsoft" button --> gets redirected to Cognito (https://{{myDomain}}.auth.{{aws-region}}.amazoncognito.com/oauth2/authorize) passing a clientId --> clientId resolved in Cognito, matched with a registered App within --> User gets redirected to the login URL defined for the app --> user concluded with the authentication --> user gets redirected to cognito --> user gets redirected to the redirect URI
The user gets redirected properly to the Microsoft Entra login page:
https://login.microsoftonline.com/organizations/oauth2/v2.0/authorize?client_id={{client_uuid}}&redirect_uri=https://{{myDomain}}.auth.{{aws-region}}.amazoncognito.com/oauth2/idpresponse&scope=openid&response_type=code&state={{state_part_1}}.{{state_part2}}.{{state_part3}}
Authentication completed and user gets redirected to the registered return URI.
I have played a bit around and if I change the Issuer in Cognito to be specific for my tenant: https://login.microsoftonline.com/{{entra_tenant_uuid}}/v2.0 - I can authenticate successfully.
Though, in case of external tenants, this will result in an error because the issuer is invalid.
Changing the issuer to https://login.microsoftonline.com/common/v2.0 -as documented-, not even I can conclude with the authentication and flow ends up in the above error.
I would appreciate any help, suggestion where to look for errors.
Thanks in advance!8 replies
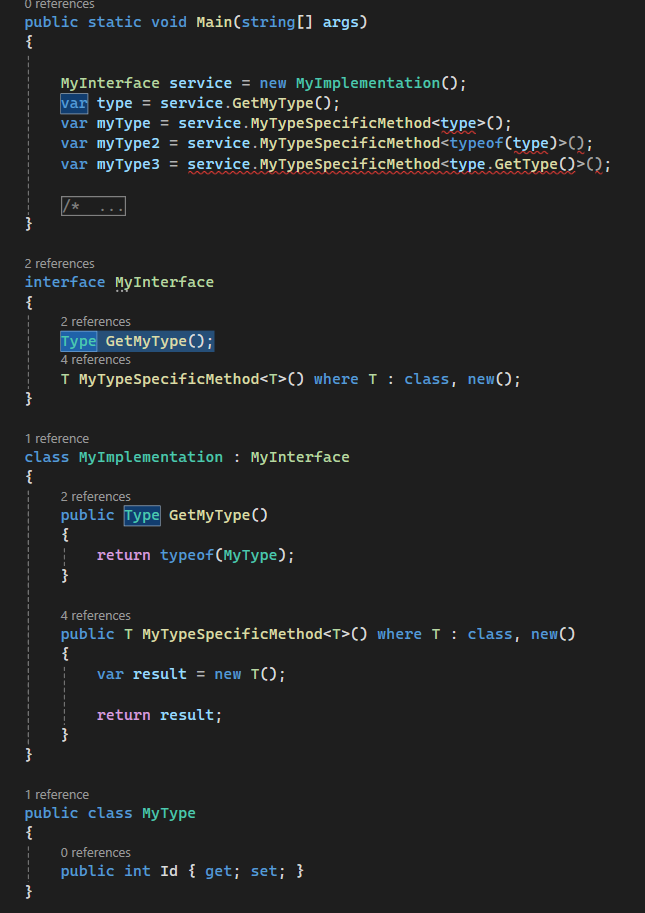
✅ .NET 8, EF Core, Fluent API - Schema definition is ignored when accessing via DbSet
HI, I would appreciate some hints where I have made the mistake. I am running an ASP.NET API. I am relying on EF Core for data accessing ORM.
The db is scaffolded with Code first approach. I have created and mapped a new Entity.
Update-Database run properly, the schema and and table created properly.
When I try to test and persist an entity, it results in error:
Error:
QQ: what am I missing making the Db operation look for the table at the default schema, instead of the specified one?10 replies
Federated authentication with Microservices - options pro/con?
Let's say we have an Authentication API (with minimal Angular frontend app) with geo replications in Cloud environment. And we have the main API supporting the user main interface which is hosted in several regions.
Our authentication flow is as the following:
1) user authenticates himself on the AUTH application with username+pw + 2FA
2) upon successful authentication, we request a token from the relevant MAIN application and redirect the user to the relevant endpoint with this token.
3) upon landing, the MAIN application verifies the token and checks with AUTH api if the logging in user is indeed the one the token was generated for.
The objective
We need to ensure that certain components of the MAIN applications are available to certain users.
Some user journey indicates a joint workflow with peers. In this process we send an invitation to the peers, which force them to get through the above auth flow.
Important 1 these peers, may be needed to join again in the future (like weeks/months later) and it is not required that the same peers will join. (maybe fewer, maybe more)
Important 2 there is always a coordinatorwho initiates the workflow. Peers cannot join without the coordinator initiating it.
The business need is, that peers do not need to get through this auth process, but has access to the content of the workflow. But only for that workflow. The business indicates the usage of some federated authentication.
Reason for that, that due to the high intervals between joining the workflow, might end up peers to forget their credentials.
2 replies