No secure hashing method?
Hello,
I got an assignment from school to save plain text passwords as a encrypted password in C#.
I have looked at the following pages:
https://learn.microsoft.com/en-us/aspnet/core/security/data-protection/consumer-apis/password-hashing?view=aspnetcore-8.0
https://andrewlock.net/exploring-the-asp-net-core-identity-passwordhasher/
And I'm rn so fuqing impressed what a piece of shiq language C# is. Is there fr no by default implemented method to securely hash Passwords?
I got an assignment from school to save plain text passwords as a encrypted password in C#.
I have looked at the following pages:
https://learn.microsoft.com/en-us/aspnet/core/security/data-protection/consumer-apis/password-hashing?view=aspnetcore-8.0
https://andrewlock.net/exploring-the-asp-net-core-identity-passwordhasher/
And I'm rn so fuqing impressed what a piece of shiq language C# is. Is there fr no by default implemented method to securely hash Passwords?
Learn how to hash passwords using the ASP.NET Core Data Protection APIs.

Andrew Lock | .NET Escapades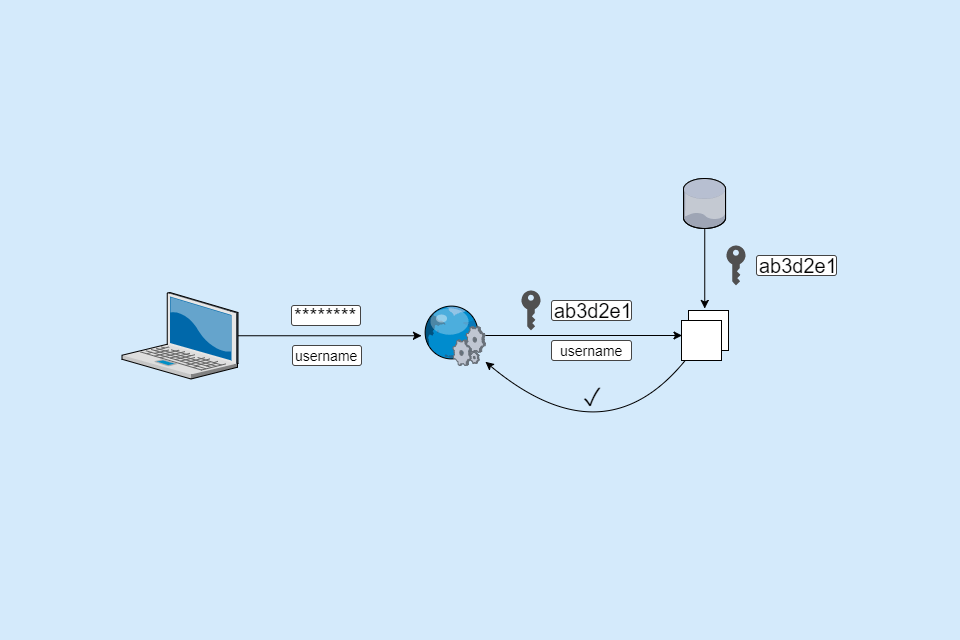
In this post I take a look at the PasswordHasher<> implementation from the ASP.NET Core Identity framework, and how it supports multiple hashing algorithms.

