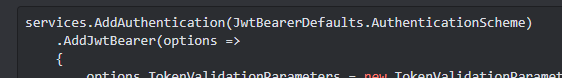
✅ Authorization in ASP.NET Web Api
[Authorize("MyApiUserPolicy", AuthenticationSchemes = "Bearer")]
How exactly does it check provided token if it is valid or not?
Like does it generate similar token and based on provided token it just compares it or there is something else going on?
How exactly does it check provided token if it is valid or not?
Like does it generate similar token and based on provided token it just compares it or there is something else going on?