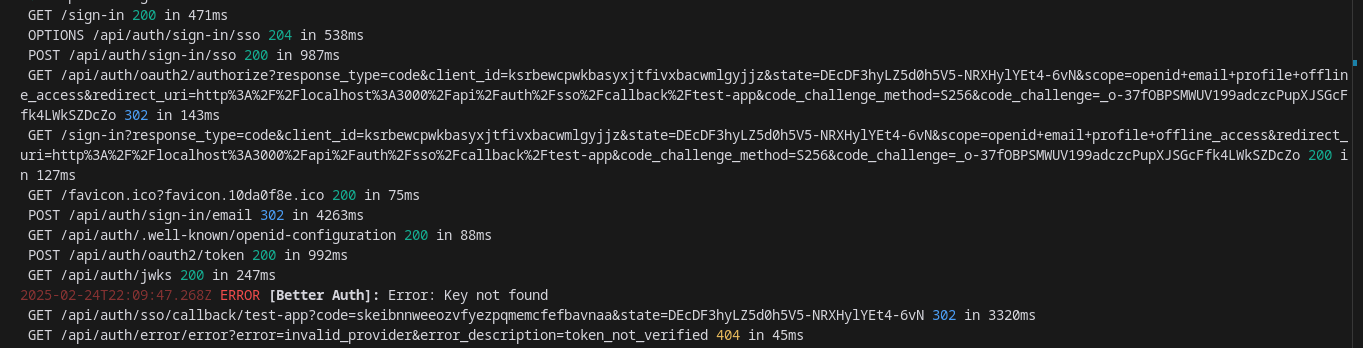
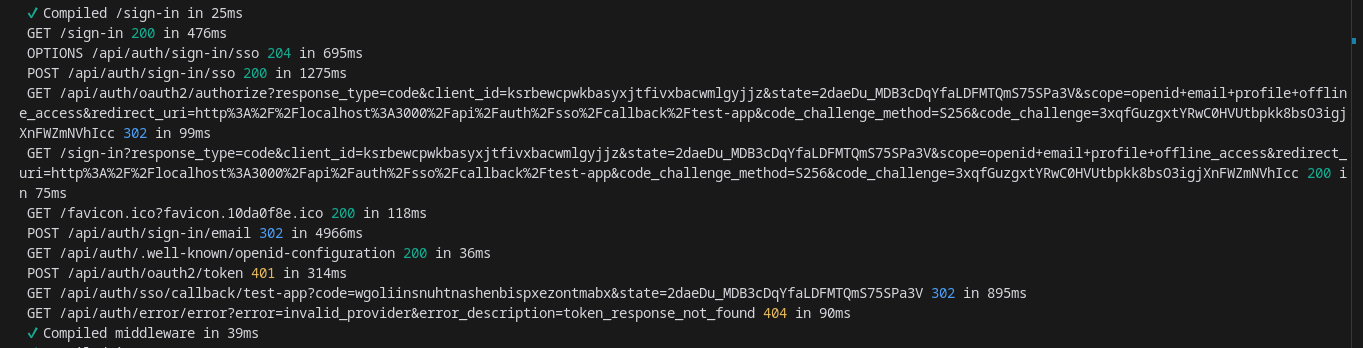
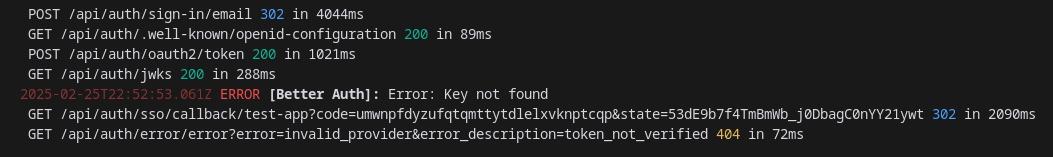
Need Help Single Sign-On (SSO) with OIDC Provider Plugin
Hey everyone! I'm integrating Single Sign-On (SSO) with Better Auth using the OIDC Provider Plugin across two Next.js apps:
Main app (Backend + Auth) → http://localhost:3000
Frontend (SSO Login UI) → http://localhost:3001
 Current Setup
Current Setup
Main App - Auth Configuration (
Main app (Backend + Auth) → http://localhost:3000
Frontend (SSO Login UI) → http://localhost:3001
 Current Setup
Current SetupMain App - Auth Configuration (
auth.tsauth.tsimport { betterAuth } from "better-auth";
import { drizzleAdapter } from "better-auth/adapters/drizzle";
import { db } from "@/db";
import {
oidcProvider,
phoneNumber,
openAPI,
admin,
organization,
jwt,
} from "better-auth/plugins";
import { sso } from "better-auth/plugins/sso";
import { authSchema } from "@/db/schema";
import { nextCookies } from "better-auth/next-js";
export const auth = betterAuth({
database: drizzleAdapter(db, {
provider: "pg", // or "mysql", "sqlite"
schema: {
...authSchema,
user: authSchema.user,
},
}),
trustedOrigins: ["http://localhost:3001"],
account: {
accountLinking: {
enabled: true,
trustedProviders: ["google", "test-app"],
},
},
user: {
additionalFields: {
jobTitle: {
type: "string",
required: false,
},
},
},
emailAndPassword: {
enabled: true,
},
socialProviders: {
google: {
clientId: process.env.NEXT_PUBLIC_GOOGLE_CLIENT_ID as string,
clientSecret: process.env.GOOGLE_CLIENT_SECRET as string,
},
},
plugins: [
phoneNumber(),
openAPI(),
organization(),
admin(),
nextCookies(),
oidcProvider({
loginPage: "/sign-in",
consentPage: "/oauth2/authorize",
requirePKCE: true,
}),
jwt(),
sso(),
]
});import { betterAuth } from "better-auth";
import { drizzleAdapter } from "better-auth/adapters/drizzle";
import { db } from "@/db";
import {
oidcProvider,
phoneNumber,
openAPI,
admin,
organization,
jwt,
} from "better-auth/plugins";
import { sso } from "better-auth/plugins/sso";
import { authSchema } from "@/db/schema";
import { nextCookies } from "better-auth/next-js";
export const auth = betterAuth({
database: drizzleAdapter(db, {
provider: "pg", // or "mysql", "sqlite"
schema: {
...authSchema,
user: authSchema.user,
},
}),
trustedOrigins: ["http://localhost:3001"],
account: {
accountLinking: {
enabled: true,
trustedProviders: ["google", "test-app"],
},
},
user: {
additionalFields: {
jobTitle: {
type: "string",
required: false,
},
},
},
emailAndPassword: {
enabled: true,
},
socialProviders: {
google: {
clientId: process.env.NEXT_PUBLIC_GOOGLE_CLIENT_ID as string,
clientSecret: process.env.GOOGLE_CLIENT_SECRET as string,
},
},
plugins: [
phoneNumber(),
openAPI(),
organization(),
admin(),
nextCookies(),
oidcProvider({
loginPage: "/sign-in",
consentPage: "/oauth2/authorize",
requirePKCE: true,
}),
jwt(),
sso(),
]
});