ERROR [AuthService] Unable to complete OAuth login: RPError: failed to validate JWT signature
Trying to setup Oauth with Authelia and I am getting this error
Authelia setup:
http://upload.montague.im/u/6JjMkY.png
Immich setup:
http://upload.montague.im/u/atj8yJ.png
41 Replies
bump
Do you have these 3 in redirect uris?
yep
And have you set Authelia up as a oidc?
https://www.authelia.com/configuration/identity-providers/open-id-connect/
yep its here
It does not seems so from your config.
You don't have any config after oidc:
You are missing all the keys and the rest of the oidc config
Then you should have
clients:
immich: etc etc
I think you might need to specify a signing algorithm
Do you mind posting the error here?
Sorry
didnt see these
I got oauth working with portainer
so idk the deal with immich, i was having an issue wher eit didnt recognize authelias secrets
so i trying one in plain text sto see if it works
i did, i put none
even with rs256 no dice
here is the error
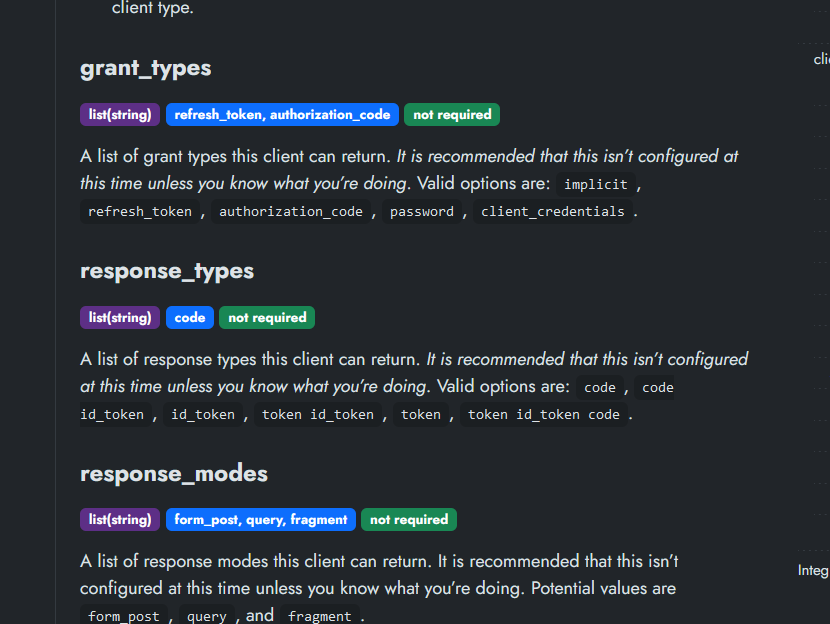
You don't have Grant type listed in your config?
I was going to say that next - you need authorization type auth code
okay ill give that a try
added this still no
looking at this it looks like things are fine on the authelia side
also looking at the docs grant_types are defined by default

Inside the immich oauth config can you try using the well known endpoint for the issuer URL. And validating that the secret you created matches.
Otherwise your setup is similar to mine and it works fine for me
I can try and post my configs later so you can compare
here's a valid config
you need to edit
hmac_secret, issuer_private_key, allowed_origins, redirect_uris, and secret
i just use docker secrets
i dont pass them in the cfg
only thing you have tha ti dont is the cors stuff
a lot of these are just the defaults you have specified
You don't need to change that much entries
ik
Do you have other services using the identity_providers ?
im just pointing out you specified things that are default
yep
portainer
portainer works
I have the feeling that something is wrong with your
issuer_private_key or your hmac_secretits gets through fien on the authelia side
and it works with portainer
why would it be any different
Does portainer check the JWT signature ?
not entirely sure
Yeah that's what that error means to me is that when decrypting on the immich side it's failing because the secret from authelia and immich isn't meshing. But that's me just guessing. Could try regenerating the auth and client secret again and redoing it. Sorry that's all I have
my guess was that
immich doesnt like argon secrets
or whatever they are called
I currently use pbkdf2. I may try Argon later and see if it works
how do i generate a secert using that
Authelia
authelia crypto hash generate pbkdf2 - Reference
Reference for the authelia crypto hash generate pbkdf2 command.
still with that encryption it didnt work
idk whats going on

What signing algorithm is being used, do you know?
on the side of authelia i specified none
Did you try with RS256?
YEP
sorry caps
And it still says failed to validate jwt?
yep :/

It looks like this case is being skipped and an error from 1083 is being thrown.
The client library we're using is pretty good so I'm pretty sure it is working as designed.
yeah i dont think its your guy's fault at all just a problem in my config, but idk wha tit is