For example I m still not quite sure
For example I'm still not quite sure whether akmods (xone, v4l2loopback,...) should be included in main or be their own image.
mainnvidiamain but that's in scope too
but that's in scope too 


main That's too obscure.
That's too obscure.
nvidia
nvidia
And great to hear that the key in the repo is just some example key.ahh... yeah, there is a TEST key checked in which is to aid in dev/testing for users trying to locally test an nvidia PR

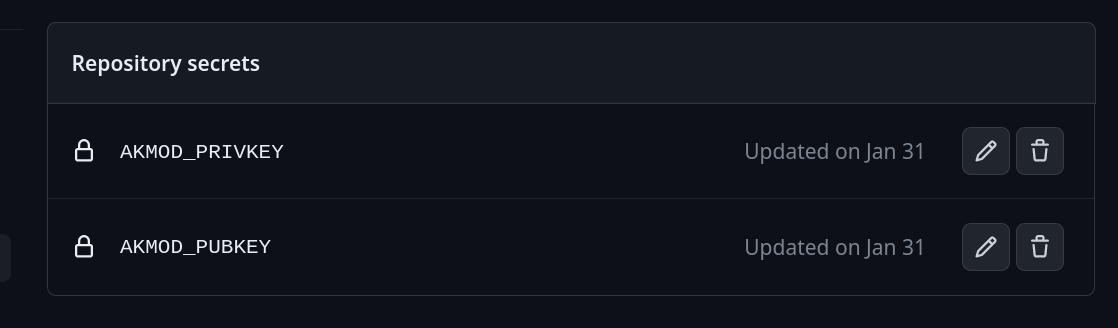
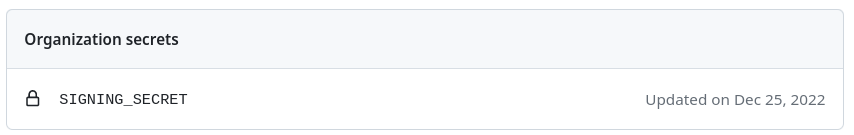


extendedextendedextendedsilverblue-nvidiaAKMOD_PRIVKEYSIGNING_SECRETucore