❔ Antiforgery token validation in API's
Antiforgery tokens are for preventing cross-site request forgery. Does that mean all sensitive API's should validate the token?
I haven't got into authentication and authorization in asp net core yet, should I learn that first and then I would become clear?
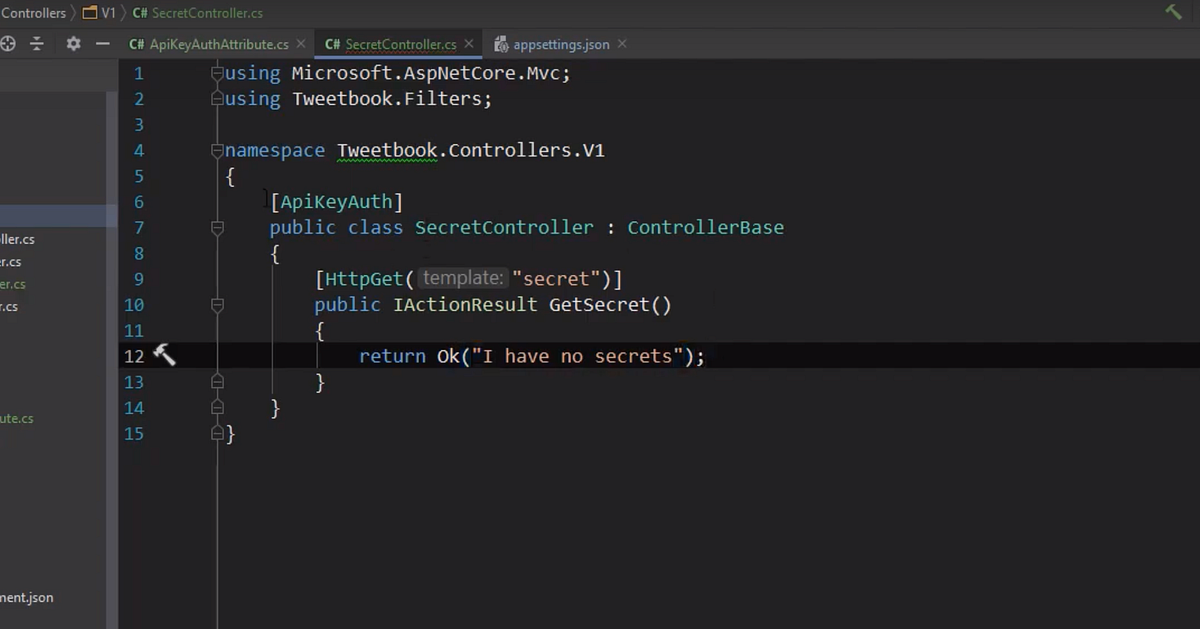
I mean, I have a razor page + api controllers app, and I was planning to use api controllers for all api-related things, so no form post request handling in the razor code. So I wonder is the authentication strategies used in the two approaches are completely different. I mean, razor pages would most likely use cookies on the client side to manage the sensitive user authentication information, while API's used in their pure form would just have a plain token, both I imagine would end up in the HTTP headers, so should they be validated in the same way? Should pure API's be trusted more? And then, isn't it possible to dynamically determine the authentication scheme, to use the same API endpoint for both sources of requests?
Again, this might become clear to me if I read some more material, however it's still vague to me for now.
I haven't got into authentication and authorization in asp net core yet, should I learn that first and then I would become clear?
I mean, I have a razor page + api controllers app, and I was planning to use api controllers for all api-related things, so no form post request handling in the razor code. So I wonder is the authentication strategies used in the two approaches are completely different. I mean, razor pages would most likely use cookies on the client side to manage the sensitive user authentication information, while API's used in their pure form would just have a plain token, both I imagine would end up in the HTTP headers, so should they be validated in the same way? Should pure API's be trusted more? And then, isn't it possible to dynamically determine the authentication scheme, to use the same API endpoint for both sources of requests?
Again, this might become clear to me if I read some more material, however it's still vague to me for now.